
ERC Advanced Grant HYDRANOS
Motivation
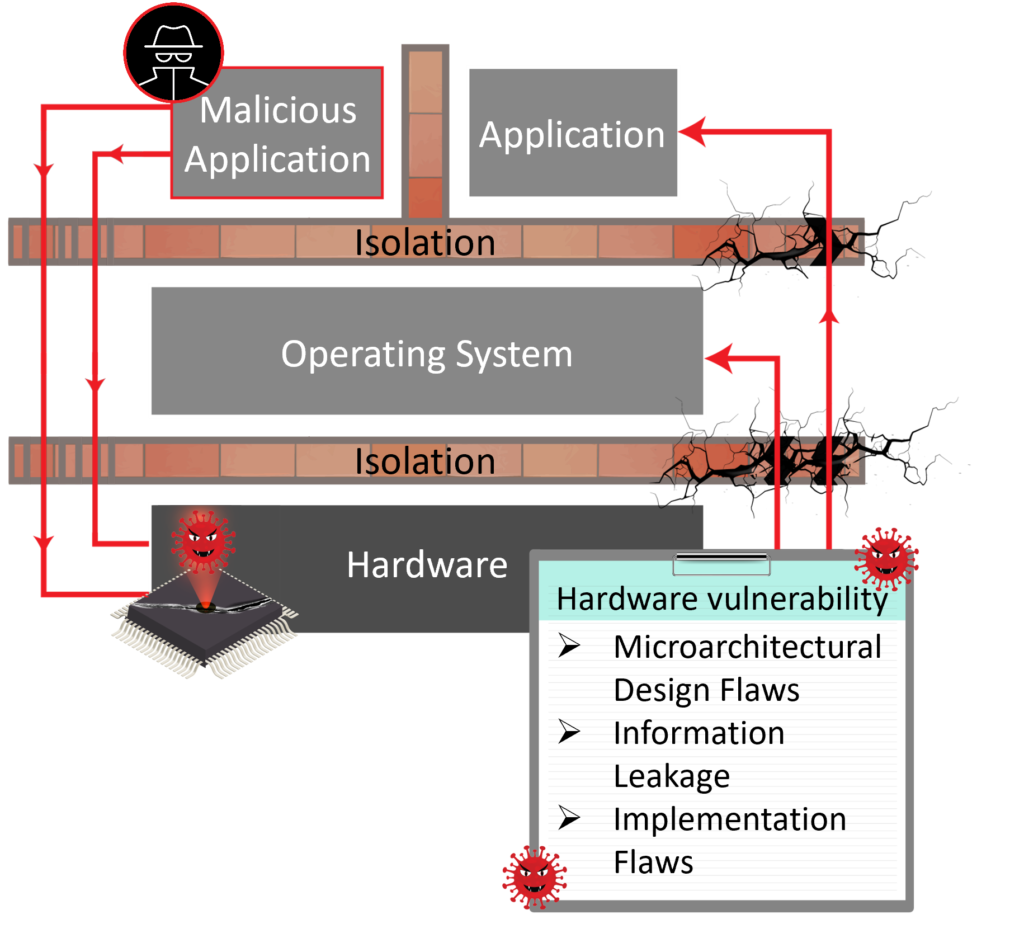
- Increasing crucial hardware vulnerabilities, particularly those that can be exploited by (remote) unprivileged software
- However, existing defences are: ad-hoc, highly limited, inefficient and customized
- Challenge: A fundamental solution requires modification of hardware which is currently not possible post-fabrication
Our vision in the ERC project HYDRANOS: A radically new security approach to overcome the current ad-hoc solution culture
HYDRANOS: Our Vision for Future of SoC Security Design
HYDRANOS presents an innovative vision centered around hardware-assisted adaptive security, signifying a paradigm shift in empowering adaptable security solutions for upcoming computing systems. Our primary objective is conceptualizing, creating, and assessing dedicated and customizable hardware components embedded within the System-on-Chip (SoC) architecture. This hardware will facilitate the post-fabrication reconfiguration of fundamental security-oriented components, offering robust mitigation against emerging attack vectors.
In addition, HYDRANOS is committed to developing a groundbreaking fuzzer meticulously tailored to pinpoint vulnerabilities spanning multiple layers within computing systems during the design phase. We aim to address critical security gaps preemptively by focusing on these cross-layer weaknesses.
The impact of HYDRANOS on establishing a foundation for trustworthy computing is profound. By its very nature, it introduces a dynamic and adaptable framework capable of effectively countering present and future cross-layer security threats that target systems of paramount importance. Through our endeavors, we aspire to contribute pioneering research that paves the way for resilient and future-proof security solutions. The outcomes of our efforts will be showcased on open-source hardware, extensively embraced by both academia and industry. We remain dedicated to providing our results to the broader research community, fostering an environment of open collaboration and third-party validation
Challenges
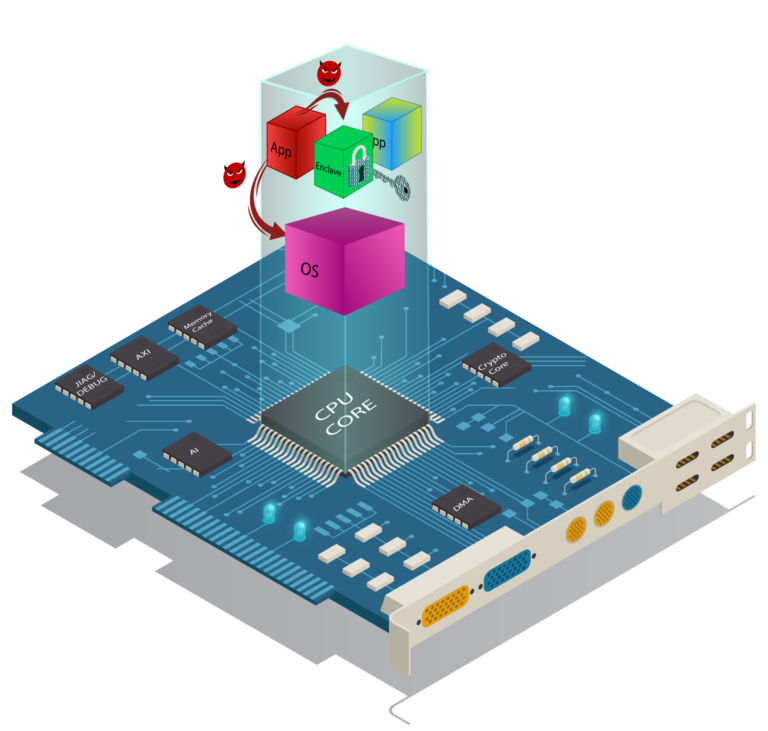
- Identification and mapping of security-relevant elements to configurable units
- Optimization strategies for security, performance, power & area trade-off of configurable units
- Validation of configuration strategies, also exploring novel hardware fuzzing methods
- Providing first open platform with adaptive security
Publications
- Wu, Lichao and Rostami, Mohamadreza and Li, Huimin and Rajendran, Jeyavijayan and Sadeghi, Ahmad-Reza. GenHuzz: An Efficient Generative Hardware Fuzzer. In: 34th USENIX Security Symposium, 2025, [Conference or Workshop Item]. Link
- Götz, Raphael and Sendner, Christoph and Ruck, Nico and Rostami, Mohamadreza and Dmitrienko, Alexandra and Sadeghi, Ahmad-Reza
RLFuzz: Accelerating Hardware Fuzzing with Deep Reinforcement Learning. In: IEEE International Symposium on Hardware Oriented Security and Trust (HOST2025), 2025, [Conference or Workshop Item] - Wu, Lichao and Rostami, Mohamadreza and Li, Huimin and Sadeghi, Ahmad-Reza (2025): HFL: Hardware Fuzzing Loop with Reinforcement Learning. In: 2025 Design, Automation & Test in Europe Conference & Exhibition (DATE), IEEE, [Conference or Workshop Item]
- Rostami, Mohamadreza and Zeitouni, Shaza and Kande, Rahul and Chen, Chen and Mahmoody, Pouya and Rajendran, Jeyavijayan and Sadeghi, Ahmad-Reza (2024): Lost and Found in Speculation: Hybrid Speculative Vulnerability Detection. In: IEEE/ACM Design Automation Conference (DAC ’24), 2024. Moscone West, San Francisco, 23. – 27. June 2024, [Conference or Workshop Item]. Link
- Rostami, Mohamadreza and Chen, Chen and Kande, Rahul and Li, Huimin and Rajendran, Jeyavijayan and Sadeghi, Ahmad-Reza (2024):
Fuzzerfly Effect: Hardware Fuzzing for Memory Safety. In: IEEE Security & Privacy 2024, pp. 2-12. IEEE, p-ISSN 1540-7993, e-ISSN 1558-4046, DOI: 10.1109/MSEC.2024.3365070, [Article]. Link - Borkar, Pallavi and Chen, Chen and Rostami, Mohamadreza and Singh, Nikhilesh and Kande, Rahul and Sadeghi, Ahmad-Reza and Rebeiro, Chester and Rajendran, Jeyavijayan (2024): WhisperFuzz: White-Box Fuzzing for Detecting and Locating Timing Vulnerabilities in Processors. In: 33rd USENIX Security Symposium, 2024, [Conference or Workshop Item]. Link
- Rostami, Mohamadreza and Chilese, Marco and Zeitouni, Shaza and Kande, Rahul and Rajendran, Jeyavijayan and Sadeghi, Ahmad-Reza (2024): Beyond Random Inputs: A Novel ML-Based Hardware Fuzzing 27. IEEE Design, Automation and Test in Europe Conference (DATE ‘24), Valencia, Spain, 25. – 27. March 2024, [Conference or Workshop Item]. Link
- Gohil, Vasudev, Rahul Kande, Chen Chen, Ahmad-Reza Sadeghi, and Jeyavijayan Rajendran. “MABFuzz: Multi-Armed Bandit Algorithms for Fuzzing Processors.” arXiv preprint arXiv:2311.14594 (2023). Link
- Chen, Chen, Vasudev Gohil, Rahul Kande, Ahmad-Reza Sadeghi, and Jeyavijayan Rajendran. “PSOFuzz: Fuzzing Processors with Particle Swarm Optimization.” In 2023 IEEE/ACM International Conference on Computer Aided Design (ICCAD), pp. 1-9. IEEE, 2023. Link
- Chen, Chen, Rahul Kande, Nathan Nyugen, Flemming Andersen, Aakash Tyagi, Ahmad-Reza Sadeghi, and Jeyavijayan Rajendran. “HyPFuzz: Formal-Assisted Processor Fuzzing.” arXiv preprint arXiv:2304.02485 (2023). Link
- Kande, Rahul, Addison Crump, Garrett Persyn, Patrick Jauernig, Ahmad-Reza Sadeghi, Aakash Tyagi, and Jeyavijayan Rajendran. “{TheHuzz}: Instruction Fuzzing of Processors Using {Golden-Reference} Models for Finding {Software-Exploitable} Vulnerabilities.” In 31st USENIX Security Symposium (USENIX Security 22), pp. 3219-3236. 2022. Link
- Chen, Chen, Rahul Kande, Pouya Mahmoody, Ahmad-Reza Sadeghi, and J. V. Rajendran. “Trusting the trust anchor: towards detecting cross-layer vulnerabilities with hardware fuzzing.” In Proceedings of the 59th ACM/IEEE Design Automation Conference, pp. 1379-1383. 2022. Link
- Jauernig, Patrick, Domagoj Jakobovic, Stjepan Picek, Emmanuel Stapf, and Ahmad-Reza Sadeghi. “DARWIN: Survival of the Fittest Fuzzing Mutators.” arXiv preprint arXiv:2210.11783 (2022). Link
- Dessouky, Ghada, Alexander Gruler, Pouya Mahmoody, Ahmad-Reza Sadeghi, and Emmanuel Stapf. “Chunked-cache: On-demand and scalable cache isolation for security architectures.” arXiv preprint arXiv:2110.08139 (2021). Link
- Kenjar, Zijo, Tommaso Frassetto, David Gens, Michael Franz, and Ahmad-Reza Sadeghi. “{V0LTpwn}: Attacking x86 processor integrity from software.” In 29th USENIX Security Symposium (USENIX Security 20), pp. 1445-1461. 2020. Link
- Dessouky, Ghada, Tommaso Frassetto, and Ahmad-Reza Sadeghi. “{HybCache}: Hybrid {Side-Channel-Resilient} caches for trusted execution environments.” In 29th USENIX Security Symposium (USENIX Security 20), pp. 451-468. 2020. Link
- Dessouky, Ghada, Shaza Zeitouni, Ahmad Ibrahim, Lucas Davi, and Ahmad-Reza Sadeghi. “CHASE: A configurable hardware-assisted security extension for real-time systems.” In 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), pp. 1-8. IEEE, 2019. Link
- Dessouky, Ghada, David Gens, Patrick Haney, Garrett Persyn, Arun Kanuparthi, Hareesh Khattri, Jason M. Fung, Ahmad-Reza Sadeghi, and Jeyavijayan Rajendran. “{HardFails}: Insights into {Software-Exploitable} Hardware Bugs.” In 28th USENIX Security Symposium (USENIX Security 19), pp. 213-230. 2019. Link
Acknowledgement

